Entra ID App Registration
5 minute read
Introduction
By registering an application, a trust relationship is established between Docusnap365 and the Microsoft Entra ID as an identity provider. Docusnap365 accesses the protected Microsoft-365 resources via a registered application.
There are two methods in Docusnap365 to add an Entra ID App Registration to the vault. The first method allows for direct creation through Docusnap365. The second method requires manual creation in the Azure Portal, but the drawback is that permissions must be configured individually.
Entra ID App Registration via Docusnap365
For an Entra ID App Registration using Docusnap365, the Entra-ID user must be in the “Global Administrators” group. Authentication and authorization are handled directly through Microsoft Entra. The Entra ID App registration can be done via the Microsoft-365 assistant, configuration settings, or the Docusnap Enterprise Gateway.
- Create App Registration:
- Click on the gear icon in the top right and navigate to “Configuration” > “Vault”. In the drop-down menu “Add”, select the option “Create Entra ID App”.
- Alternatively: Register via the “Microsoft 365” discovery assistant or the Docusnap Enterprise Gateway.
- Enter data in the dialog window:
- App Name: Allows input of letters (a - z, A - Z), special characters, spaces, and numbers.
- Primary Domain/Tenant ID: This information can be found in the Azure Portal under “Microsoft Entra ID”.
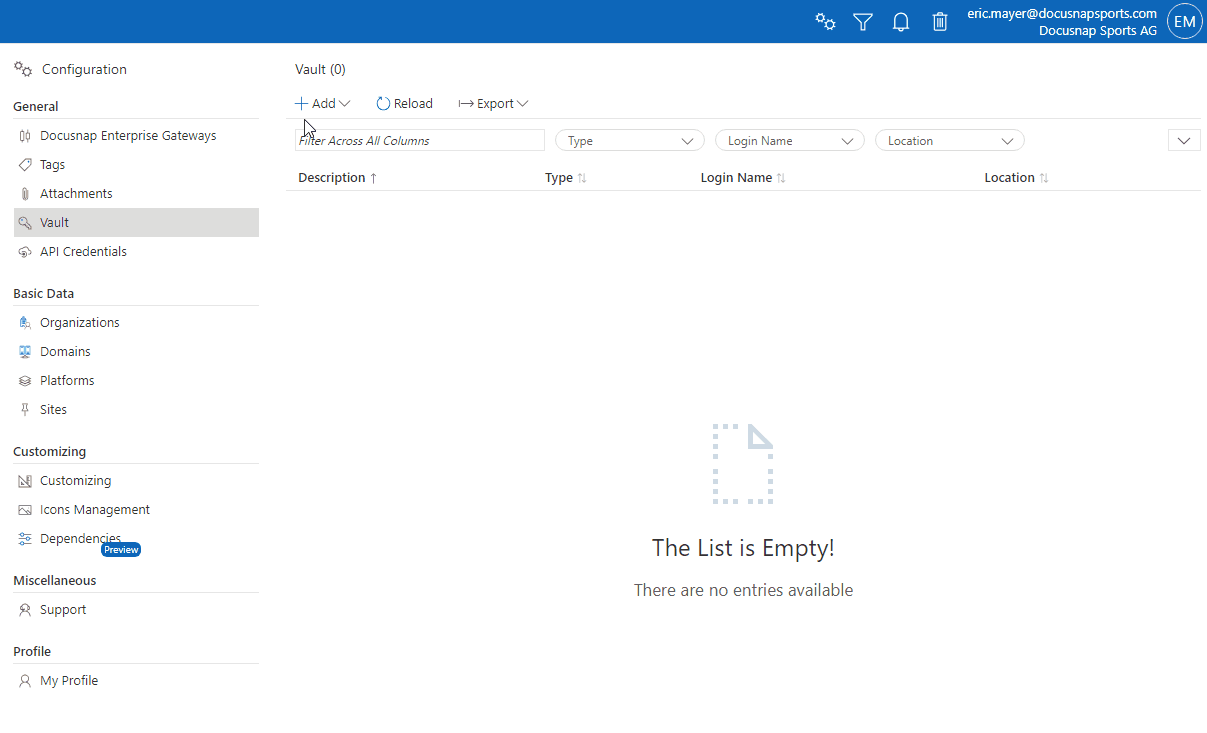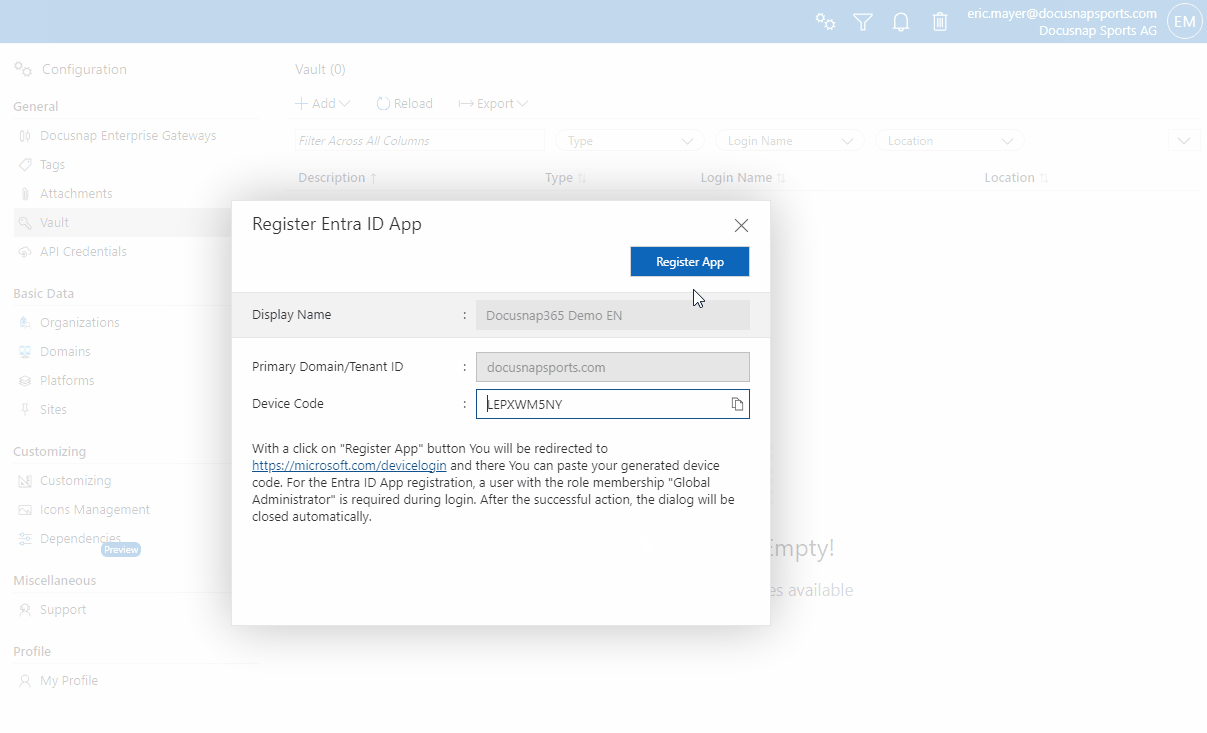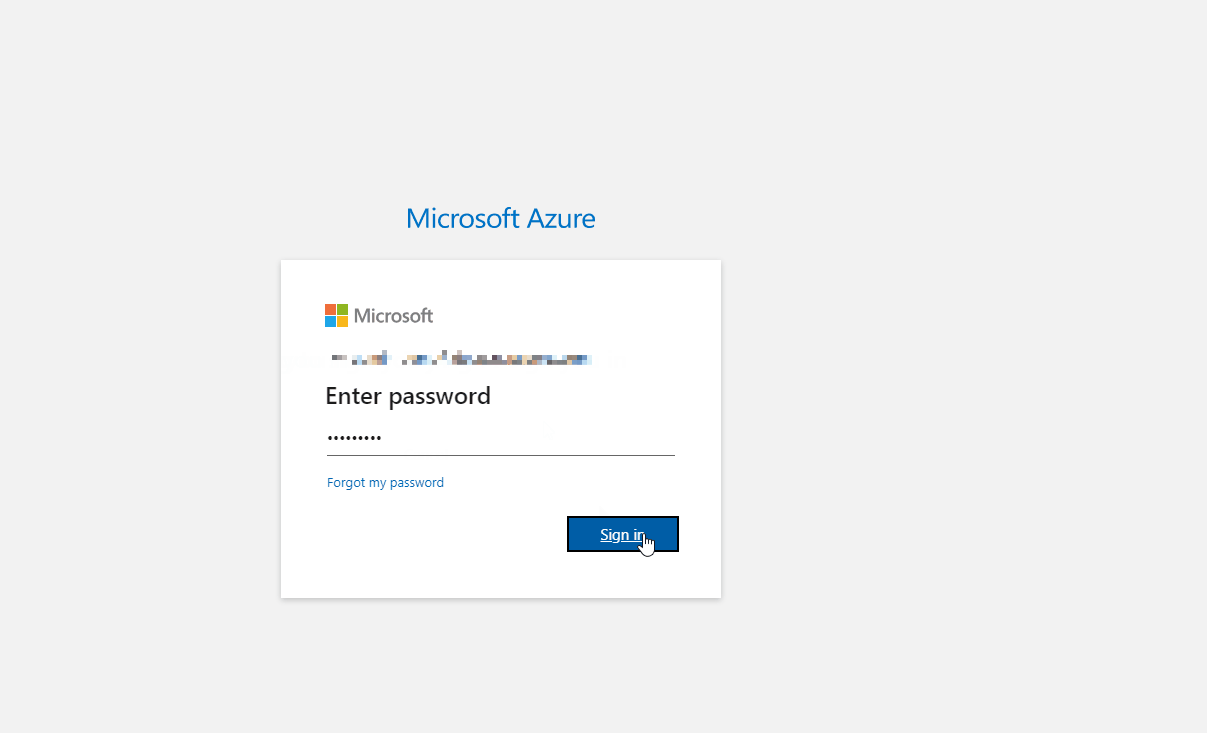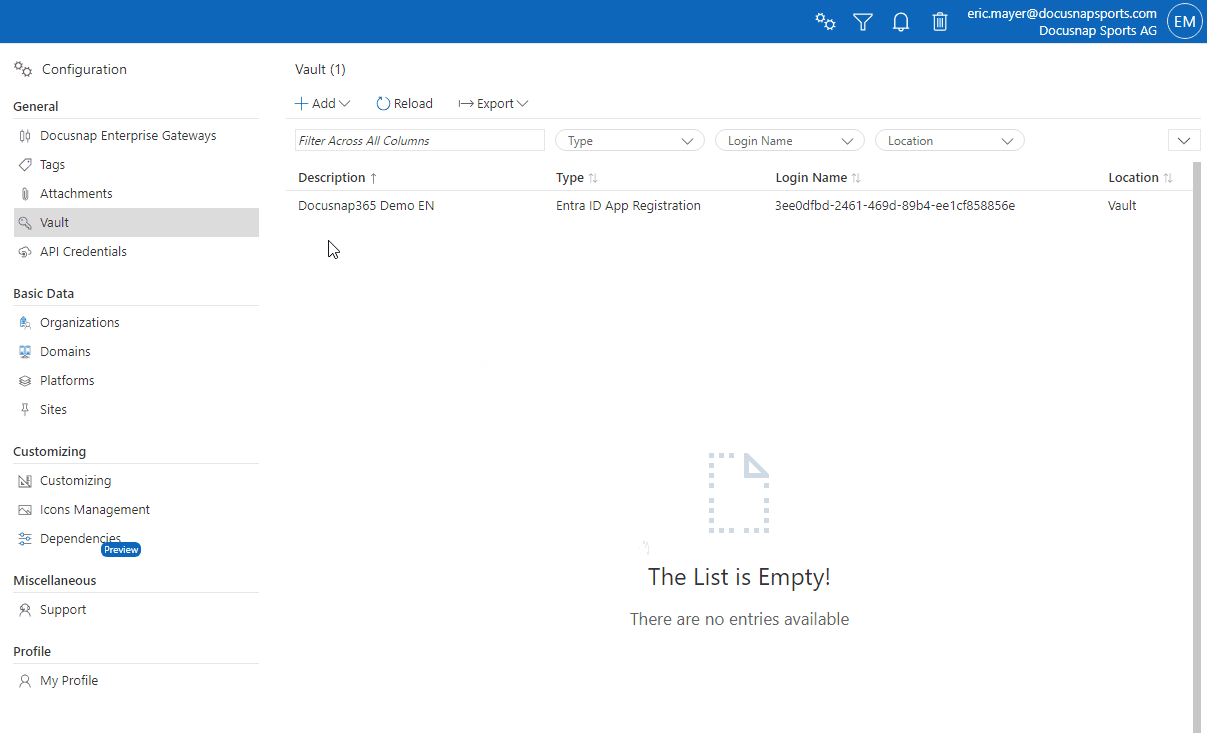
- Generate device code:
- Click on “Create Device Code”. The code is automatically copied to the clipboard but can also be copied manually.
- Verify Entra ID App:
- After clicking “Register Entra ID App”, a new browser tab opens for entering the device code.
- Sign in to the Azure Portal:
- Sign in to the Azure Portal to complete the app registration.
- Confirm sign-in:
- Confirm the “Sign in via Microsoft Azure CLI”.
After completing the steps, a new entry for the registered app appears in the Docusnap365 vault list.
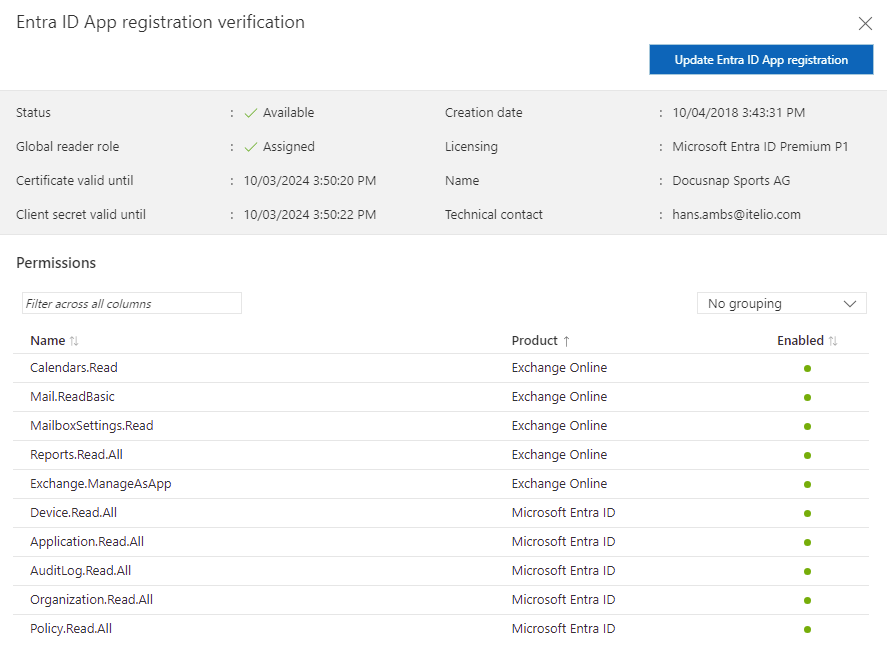
Verify Entra ID App Registration
Checking an Entra ID App registration allows for verifying certificates, key information, and permissions. The procedure for this is identical to creating a new app registration: generate device code, verify device code, sign in to the Azure Portal, and confirm the sign-in.
Update Entra ID App Registration
When creating Entra ID App registrations, we always secure them with a certificate and client secrets. Currently, we only assign permissions that are necessary for discovery, following the principle: “As little as possible, as much as necessary”. With extensions, additional permissions may be required. Certificates, client keys, and permissions can be updated as needed to keep them up-to-date. The procedure is identical to creating a new app registration: generate device code, verify device code, sign in to the Azure Portal, and confirm the sign-in.
Manual Creation of Entra ID App Registration
- Manually create app registration:
- Click on the gear icon in the top right and navigate to “Configuration” > “Vault”. In the drop-down menu “Add”, select the option “Add Entra ID App”.
- Enter data in the dialog window:
- App Name: Allows input of letters (a - z, A - Z), special characters, spaces, and numbers.
- Primary Domain/Tenant ID: This information can be found in the Azure Portal under “Microsoft Entra ID”.
- Application (client) ID: This information can be found in the Azure Portal in the manually created app registration.
- Certificate and Certificate Password: The certificate used in the app registration and the corresponding password.
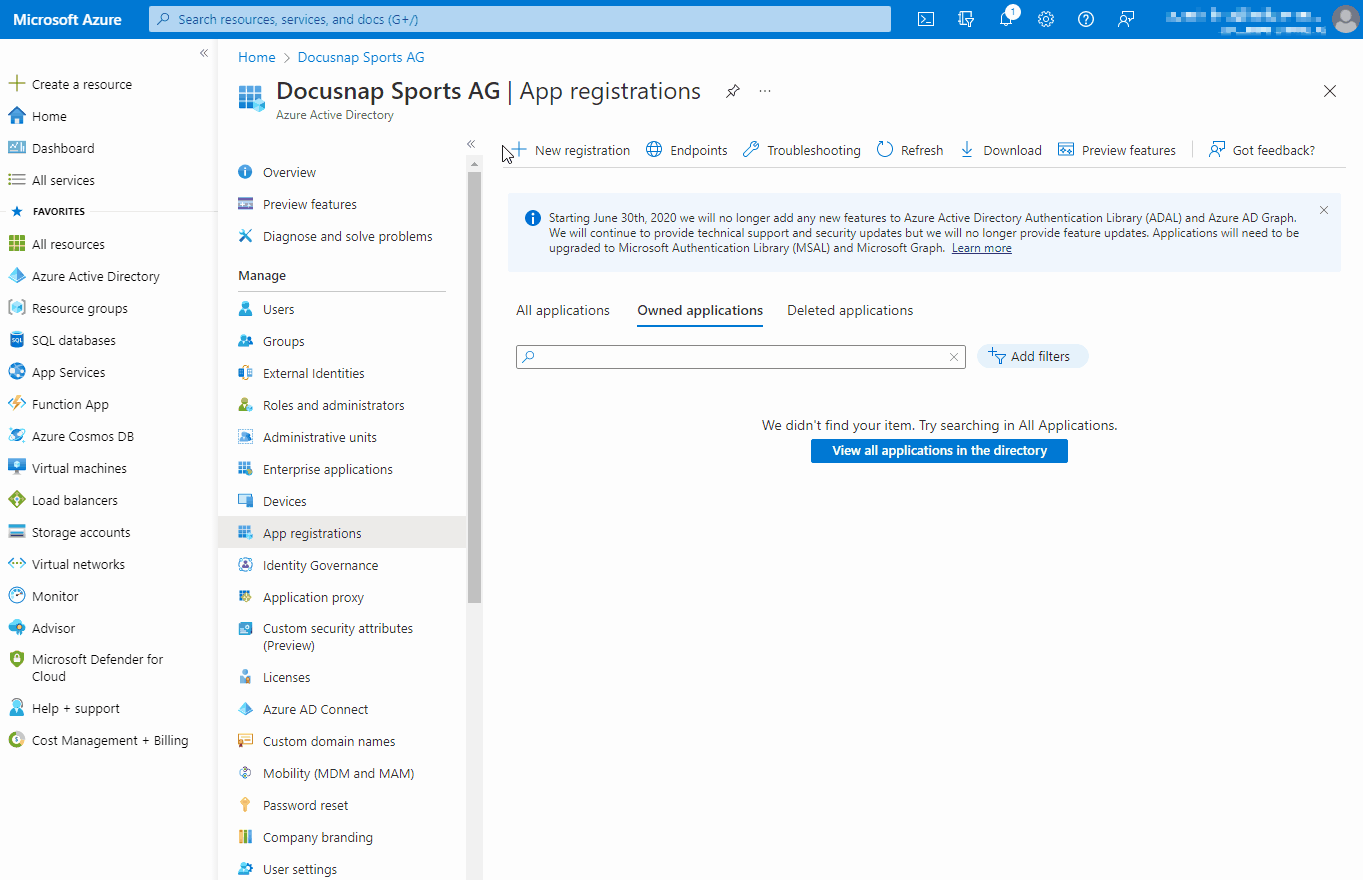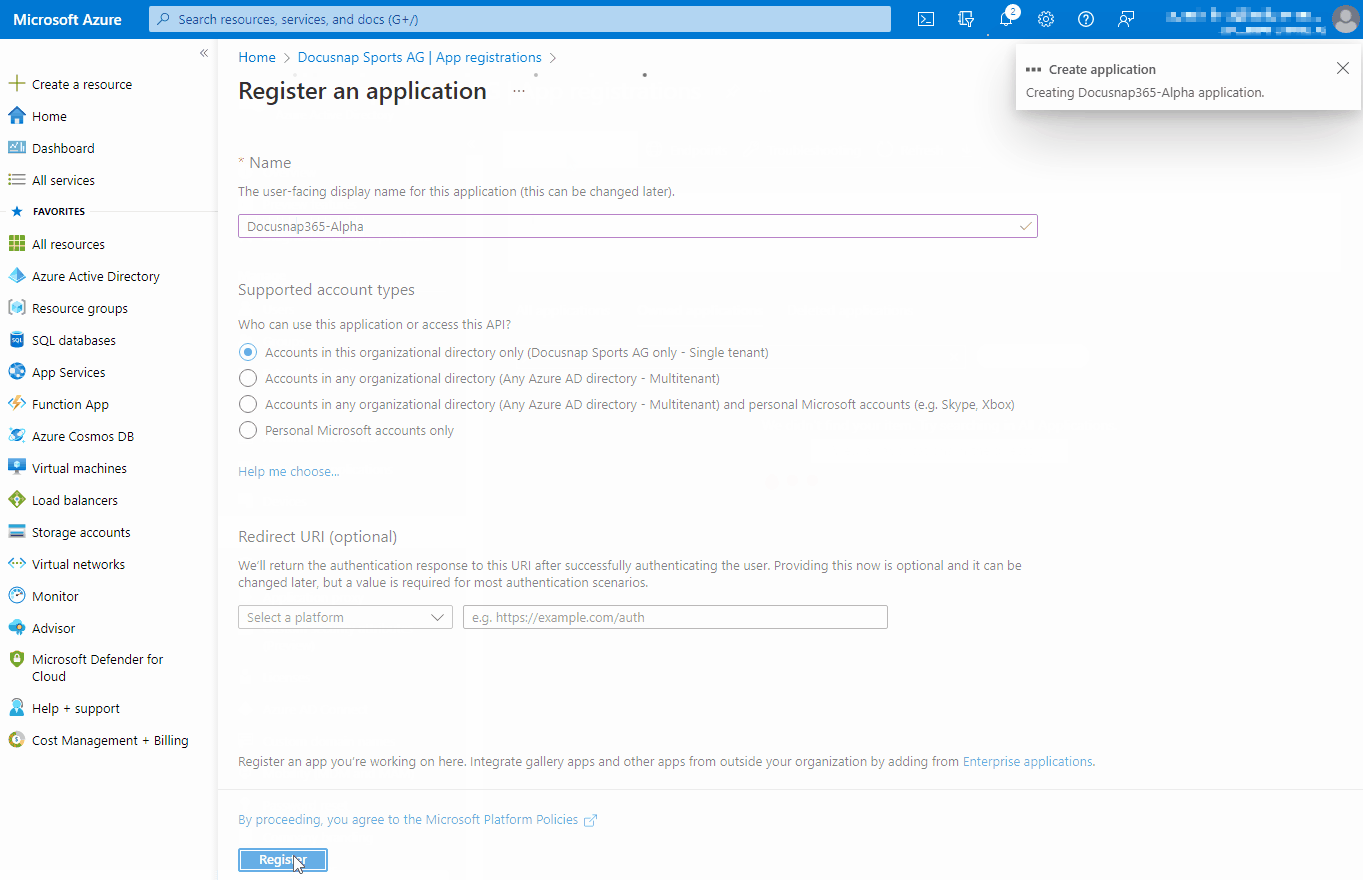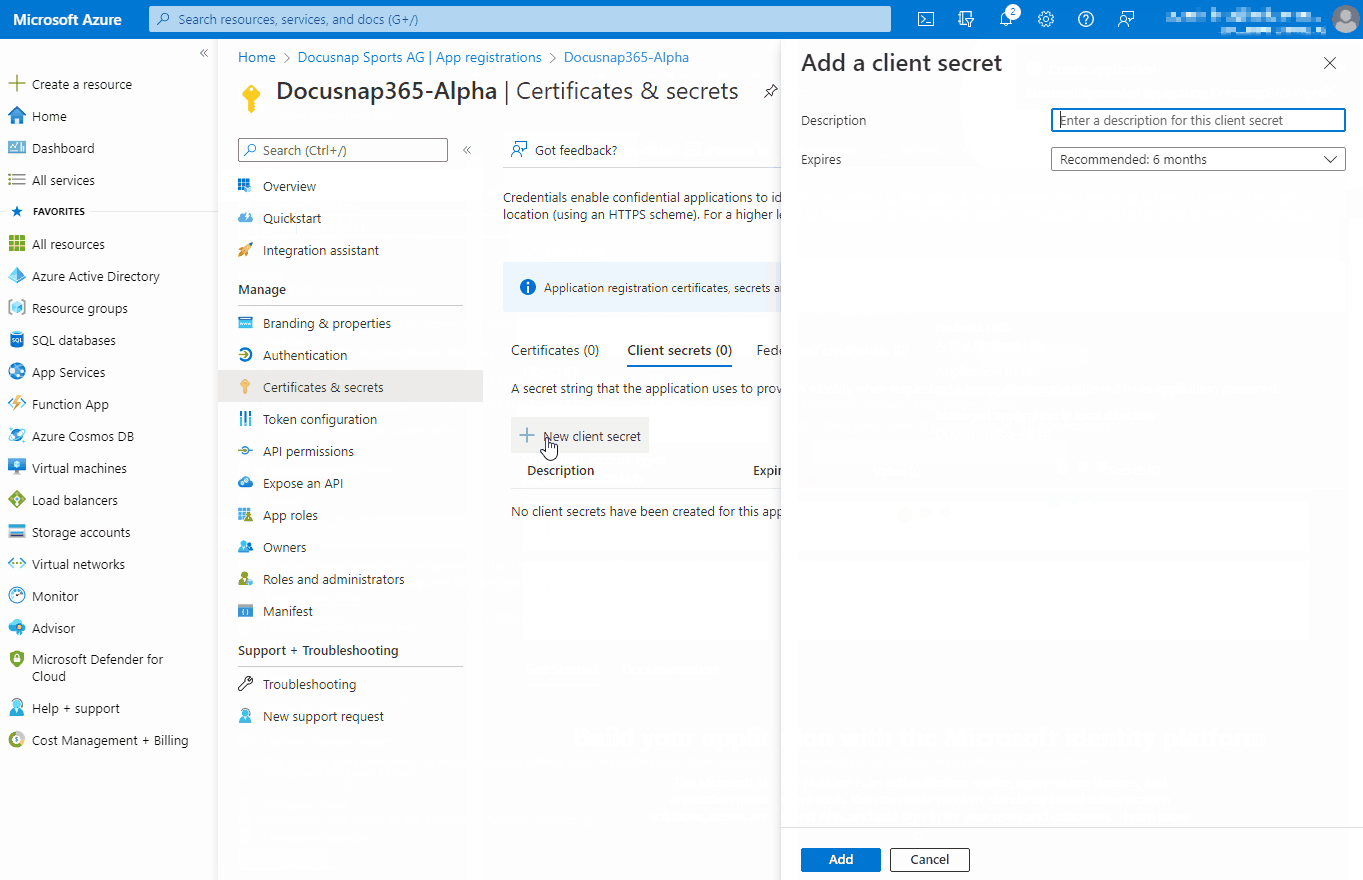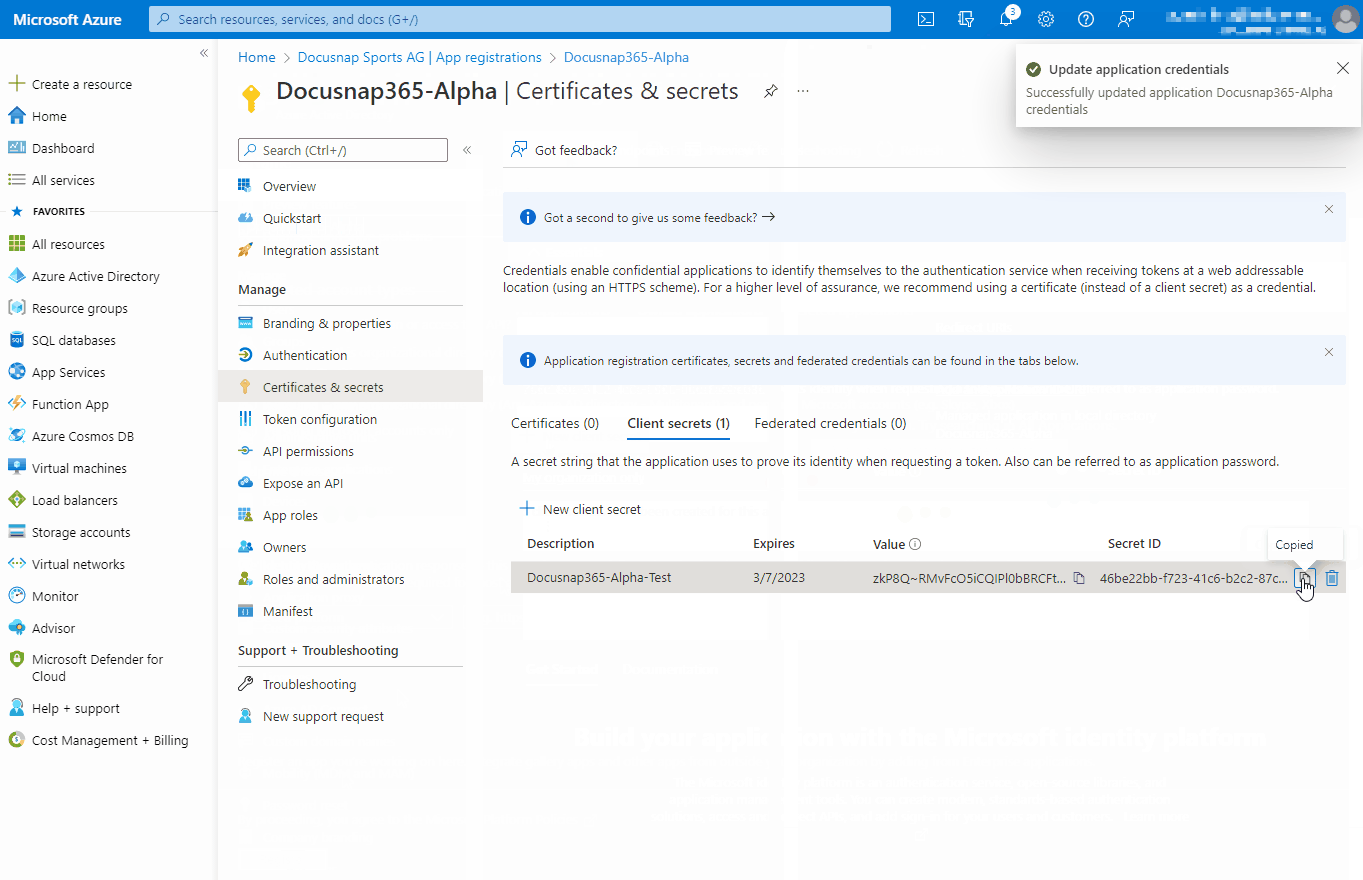
- Client Secret: The client key is only visible once during the creation of the app registration.
To establish a connection, the following information from the Entra ID App Registration is necessary:
- “Primary Domain/Tenant ID:”
- “Application ID (Client)”
- “Client key”
The registration of an application is done via the Azure Portal (portal.azure.com), in the Microsoft Entra ID section under the menu item “App Registration”.
Registering an application
API Permissions
To access a protected resource such as Teams information or SharePoint web pages, Docusnap365 needs authorization from the resource owner. Docusnap365 needs read-only access for Microsoft 365 discovery.
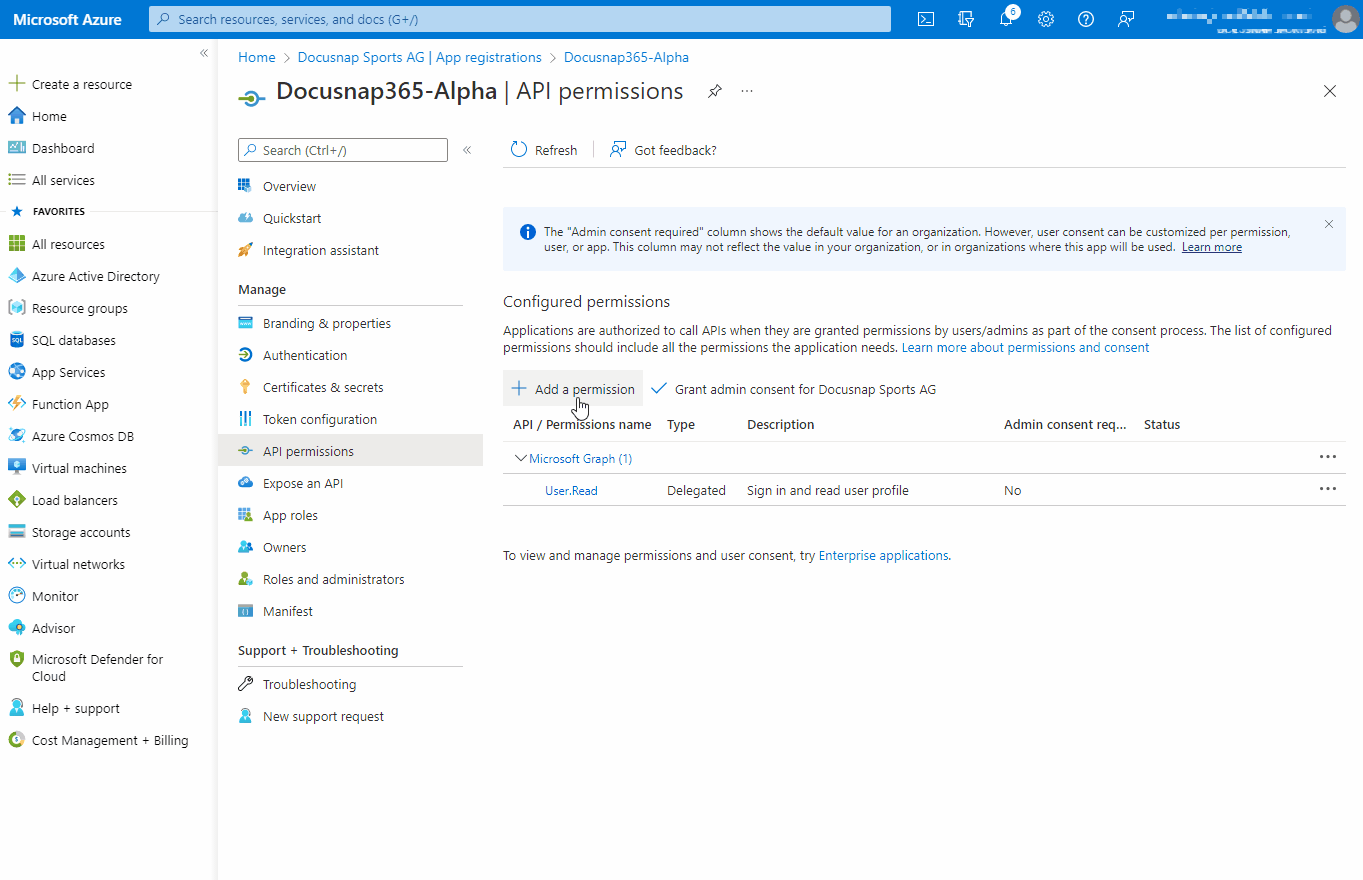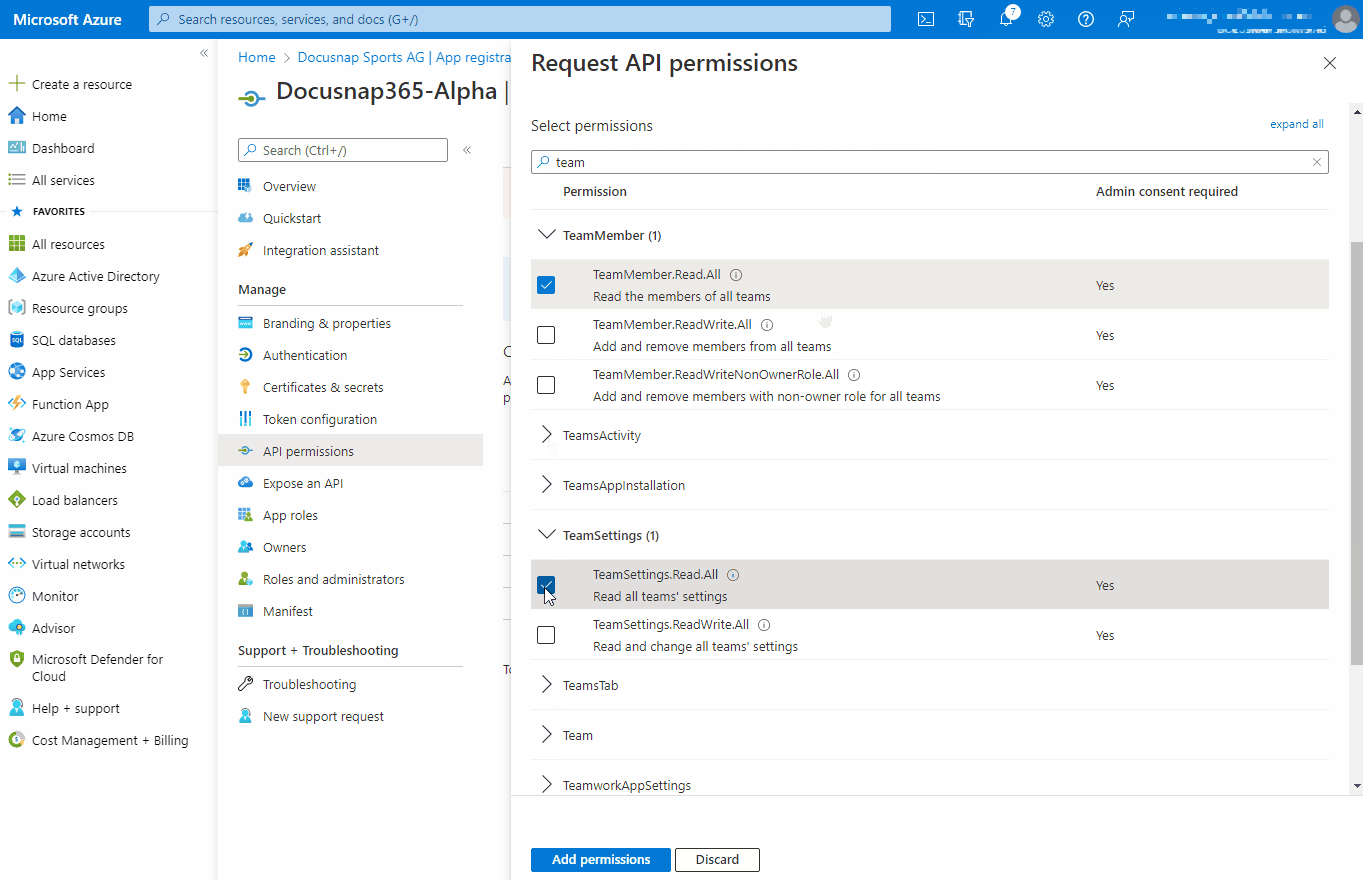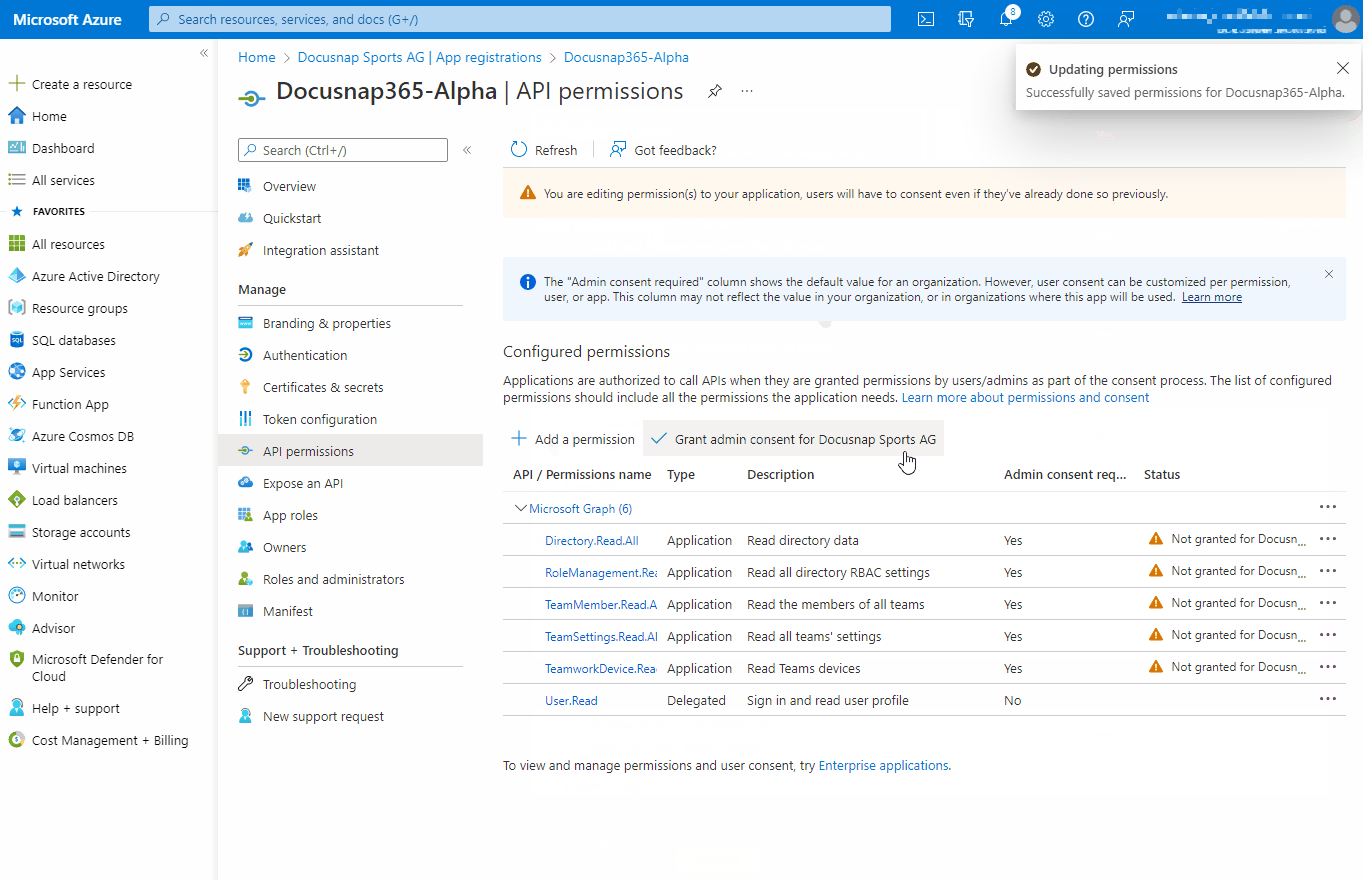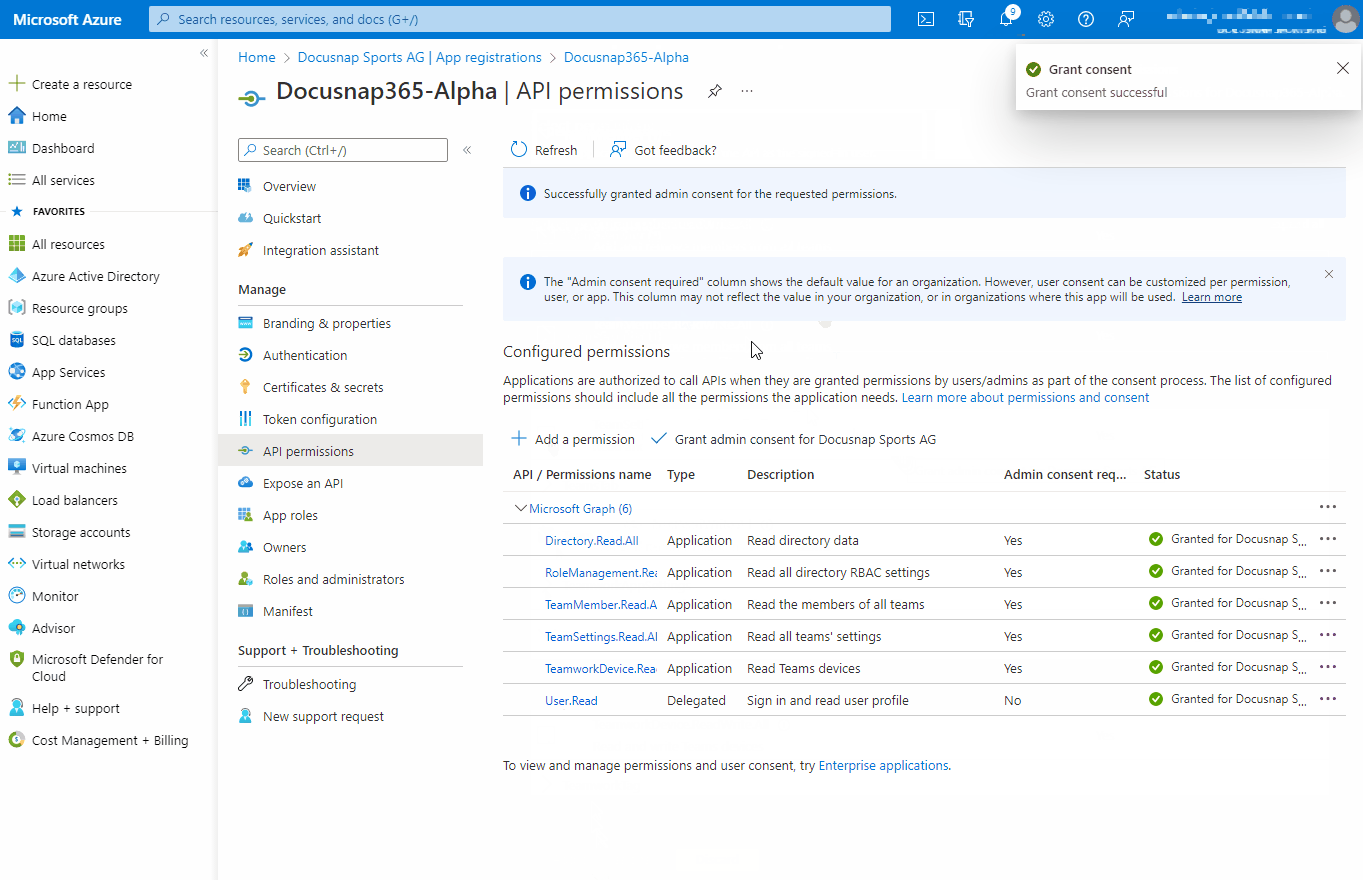
| API/Permission Name | Type | Description |
|---|---|---|
| AppCatalog.Read.All | Application | Read all app catalogs |
| Application.Read.All | Application | Read all applications |
| AuditLog.Read.All | Application | Read all audit log data |
| Calendars.Read | Application | Read calendars in all mailboxes |
| Channel.ReadBasic.All | Application | Read the names and descriptions of all channels |
| ChannelMember.Read.All | Application | Read the members of all channels |
| ChannelSettings.Read.All | Application | Read the names, descriptions, and settings of all channels |
| Contacts.Read | Application | Read contacts in all mailboxes |
| Device.Read.All | Application | Read all devices |
| Directory.Read.All | Application | Read directory data |
| Files.Read.All | Application | Read files in all site collections |
| GroupMember.Read.All | Application | Read all group memberships |
| Mail.ReadBasic | Application | Read basic mail in all mailboxes |
| MailboxSettings.Read | Application | Read all user mailbox settings |
| Organization.Read.All | Application | Read organization information |
| Policy.Read.All | Application | Read your organization’s policies |
| Reports.Read.All | Application | Read all usage reports |
| RoleManagement.Read.Directory | Application | Read all directory RBAC settings |
| SharePointTenantSettings.Read.All | Application | Read SharePoint and OneDrive tenant settings |
| Sites.FullControl.All | Application | Have full control of all site collections |
| Sites.Read.All | Application | Read items in all site collections |
| Team.ReadBasic.All | Application | Get a list of all teams |
| TeamMember.Read.All | Application | Read the members of all teams |
| TeamSettings.Read.All | Application | Read all teams settings |
| TeamsTab.Read.All | Application | Read tabs in Microsoft Teams |
| TeamworkDevice.Read.All | Application | Read Teams devices |
| TeamworkTag.Read.All | Application | Read tags in Teams |
| User.Read | Delegated | Sign in and read user profile |
| User.Read.All | Application | Read all users full profiles |
| UserAuthenticationMethod.Read.All | Application | Read all users authentication methods |